Introduction
On June 27, 2017, a red and black skull flashed across hundreds of PCs across the world. The malware, known as NotPetya, spread rapidly and indiscriminately, integrating tools of EternalBlue and Mimikatz in a virulent combination.[1] The malware cost companies, like US-based Merck and Mondelez, millions of dollars.[2] To recuperate some of the damages, both companies filed property insurance claims with providers—all of which were denied. Specifically, Merck sued for reimbursement from over a dozen insurance companies in New Jersey, while Mondelez has challenged their insurance provider Zurich in Illinois.[3],[4] Zurich has cited the “war exclusion” clause in their policy to avoid payouts. However, two questions need answers before determining whether the insurance companies were justified in not providing reimbursements. First, does NotPetya qualify as an act of war? Second, should the war exclusion clause apply? As the ruling on the case Mondelez International v. Zurich American Insurance Company approaches, one must consider what constitutes an act of war, the purpose of the NotPetya attack, and what applies to the war exclusion clause. Given NotPetya’s intent and impact, the attack falls within criminal activity rather than a warlike act. Thus, the war exclusion clause should not apply, and insurance companies should have to pay for damages incurred from NotPetya.
What Is War
NotPetya does not fit the three essential criteria of war that Clausewitz outlines in On War. Clausewitz states war requires violence, means to an end, and political motivation.[5] NotPetya did not result in loss of life or physical injuries, failing to meet the first of Clausewitz’s criteria, physical violence.
Further, NotPetya fell short of achieving means to an end. Clausewitz suggests that means are violence, or threat of violence, and end is to render an enemy defenseless, having successfully compelled them to one’s will.[6] Although NotPetya’s end goal is murky, as only the attackers can clarify their intentions, it is likely the goal was not reached. This is demonstrated through who and what NotPetya impacted. Despite NotPetya likely originating from Russia, Russian actors and companies also incurred significant losses from the attack.[7] This indicates unanticipated damages, as it is unlikely Russia’s end goal would include harming their own companies, and it is possible that the accidental nature of these consequences extended to other victims like US companies. Moreover, despite significant interruption of systems, NotPetya did not render any country defenseless, meaning the attack fails to meet Clausewitz’s second criteria. The attack had largely financial consequences and left military operations intact. The extent of NotPetya’s impact will be discussed later in this piece.
Finally, Russia did not claim responsibility for NotPetya, hence dismissing Clausewitz’s last requirement of political motivation.[8] As Thomas Rid clarifies, “to be political, a political entity or a representative of a political entity… has to have an intention, a will. That intention had to be articulated. And one side’s will had to be transmitted to the adversary at some point during the confrontation.”[9] By not communicating their intention during NotPetya, and not admitting to the attack, the final criteria of war is also unfulfilled. Thus, NotPetya was not an act of war.
Modern Interpretations
Although some argue that Clausewitz’s definition of war is outdated, NotPetya also does not apply to modern definitions of what constitutes war. While no standard characterization exists for what establishes war, an act of war, or warlike activity in cyber, many US officials have suggested definitions. For example, former Undersecretary of Defense (Intelligence) Marcel Lettre states, “cyberattacks that proximately resulted in a significant loss of life, injury, destruction of critical infrastructure, or serious economic impact should be closely assessed as to whether or not they would be considered an unlawful attack or an ‘act of war.’”[10] Some of these criteria overlap with Clausewitz’s, like loss of life, injury, and destructionof critical infrastructure, but none of these conditions occurred during or after NotPetya.[11] However, other criteria are newer, like “serious economic impact.” NotPetya could potentially fit into this category. To evaluate if NotPetya constituted a “serious economic impact,” one must assess the costs of the attack and compare it to other warlike cases.
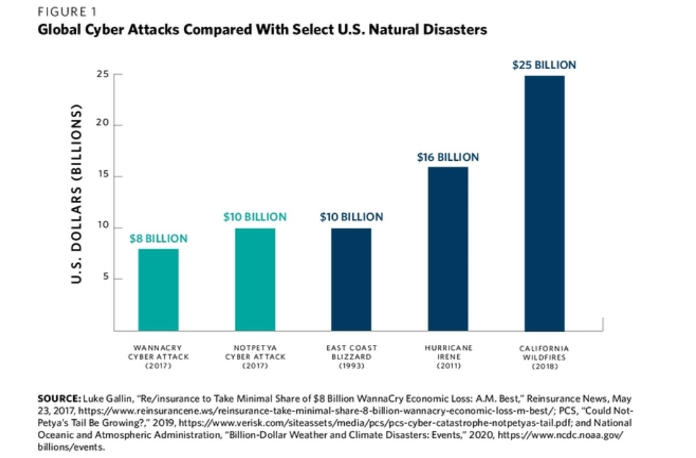
Figure 1 below shows the global cost of NotPetya totaled $10 billion. Yet when comparing this number to other unexpected events in US history, this number does not constitute a “serious” economic impact; it does not even reach half of the destruction of the California wildfires from 2018. Additionally, this graph displays the global impact of NotPetya, not just the impact on the United States. Thus, when factoring in Merck and Mondelez’s reported losses of $870 million and $188 million, the US impact from NotPetya shrinks from $10 billion to roughly $1 billion.[12] When compared to other potentially “warlike” cases like 9/11—which resulted in $7 billion to pay the Victims Compensation Fund, $28.1 billion to replace infrastructure in New York City, and $40 billion in insurance losses—NotPetya only equates to 0.01% of 9/11 costs.[13],[14] As James Lewis articulates, “[while] opportunity costs (lost sales, lower productivity, etc.) make up a large portion of reported costs of cyberattacks…opportunity costs do not directly translate into costs to the national economy.”[15] Therefore, in terms of cost analysis, NotPetya cannot qualify as an act of war since it did not significantly harm the US economy as a whole.
Political Reluctance
NotPetya does not fulfill any traditional or modern requirements to be deemed an act of war, and US political discourse supports this claim. Within US politics, there is a reluctance to call cyberattacks acts of war due to difficulty of gauging intent, or “end” as Clausewitz would put it, of cyberattacks.[16] For example, following the Sony Entertainment cyberattack in 2014, President Obama stated, “no, I don’t think it was an act of war. I think it was an act of cyber-vandalism that was very costly.”[17] Sony’s insurance providers seemed to agree with Obama, fully covering the costs of the attack.[18] The Sony Entertainment attack and NotPetya share key characteristics: non-violent acts that inflicted economic damage to a private corporation. If officials did not deem Sony Entertainment an act of war, neither should they declare NotPetya as one. Given the precedent of what constitutes an act of war, NotPetya follows similar trends more closely akin to cybercrime than a “hostile or warlike” act.
Categorizing NotPetya
While NotPetya was not an act of war, the intricacies of the attack—its technical design, target, and timing—all point to NotPetya as an act of cybercrime. Note that unless the Russian government confirms it executed NotPetya, analyses can only make inferences from outcomes. Regarding technical design, NotPetya combined ransomware with the ability to proliferate across a network.[19] Able to spread through Ukrainian accounting software Me.Doc’s backdoor disguised as an update, NotPetya circumvented whitelisting, which limits what can be installed on a computer.[20] Once in the backdoor, NotPetya’s code enabled it to spread quickly. As Me.Doc is one of two accounting softwares approved by the Ukrainian government, NotPetya swiftly proliferated across Ukraine, impacting up to 80% of businesses within the country.[21] NotPetya’s technical design suggests that this attack intended to shut down everyday operations of its target: Ukraine; utilizing Me.Doc as its backdoor, a software specific to Ukraine, points to disruption of Ukrainian business as NotPetya’s target or end goal (although the Russian government has not confirmed this). Further, the timing of the attack supports the assumption that Ukraine was NotPetya’s planned victim; NotPetya occurred just before Ukrainian Independence Day. As Russia is engaged in war with Ukraine, the mass infiltration into the business operations of Ukraine on the day of their independence sends a signal that Russia has authoritative control over Ukraine. Ukrainian officials have supported this claim, stating that the NotPetya attack “directly targeted Ukraine.”[22]
A counterpoint could argue that this attack constitutes an act of war since Russia and Ukraine are at war, and as such Zurich can claim exclusion. However, was this an act of war against the United States? When examining the aforementioned evidence, considering the backdoor target and timing of the attack, as well as the likely unintended spillover to Russian companies, the effects on US companies were probably an unforeseen consequence. Moreover, neither traditional nor modern definitions of war acknowledge unintentional consequences as an act of war. Thus, NotPetya better fits the description of a cybercrime rather than of an act of war regarding its impact on the United States.
Day in Court
It is unlikely that the court will declare NotPetya as an act of war. This is because Zurich and other insurance agencies face an upward battle proving the war exclusion clause applies. The burden of proof is overwhelmingly on the insurance providers in cyberattack cases. While war exclusion clauses in property law have a rich history in the United States, which initially favors Zurich, this number significantly dwindles in the cyber realm. A study conducted by Daniel Woods and Jessica Weinkle in 2020 analyzed the history of cyber-related insurance lawsuits within the United States. The study found that often cyber-specific qualifiers within the insurance language only applied to cyber-terrorism cases (12/56 cases) rather than cyberattacks or cybercrime.[23] While the outcome of Mondelez International v. Zurich American Insurance Company remains undecided, Williams and Weinkle’s analysis overwhelmingly found that “cybersecurity-specific terms are not used to exclude coverage via war clauses and, in fact, cyber terms were only used to expand coverage.”[24] This suggests that Mondelez and Merck will likely win their lawsuits.
A relevant precedent for war and insurance arises from Pan American World Airlines v. Aetna Casualty (1973). This case established a three-prong test for war exclusion applications that Zurich must prove. From this case, NotPetya must be a hostile act, part of a course of hostility, and committed by actors with significant attributes of sovereignty for the insurance provider to deny coverage.[25] Zurich hopes this broad interpretation of “hostile or warlike action” covers any state-sponsored incident within the cyber context. Additionally, since both Merck and Mondelez possess insurance policies with exclusion language that states the insurance companies can deny coverage if “hostile or warlike action in time of peace or war… whether carried out by a government or its agent” occurs, Zurich in Mondelez’s case wants the umbrella term of war exclusion to encompass the events of NotPetya.[26]
Yet, in the same 1973 case, the New York court ruled against the insurance provider and the war exception clause. The court stated the defendant did not prove the necessary criteria to characterize the event as an act of war. This happened because the burden of proof was insurmountable for Aetna Casualty. The court specified, “civilian citizens of non-belligerent powers and their property at places far removed from the locale or the subject of any warfare” would not qualify as “warlike operations.”[27] This case mirrors the events of NotPetya, as the attack was likely directed at Ukraine, which is “far removed from the locale” and therefore does not qualify.
Additionally, despite this flexibility in the Merck and especially Mondelez policies, applying war exclusion to cyberspace remains difficult. This complexity stems from issues surrounding burden of proof and attribution. Attribution is a convoluted issue within cybersecurity, where no universal process and procedure exist. Jon Bateman concludes, “unlike courts, different intelligence services might offer competing assessments of the same incidents.”[28] This makes linking attribution to war exclusion extremely complex and requires the insurance companies to solve this issue that generally plagues the information security space with the added complexities of court-required proof.
Moreover, attribution is core to both Merck and Mondelez’s insurance policies. The policy’s attribution requirements call for Zurich to first identify the perpetrator and second that they acted under state authority.[29] Despite attribution appearing easy in the NotPetya case, as the US government has attributed NotPetya to Russia’s GRU unit Sandworm, it is actually more complex.[30] While experts can attribute incidents to specific groups and suspected national affiliation, it is unclear if this is enough for courts.[31] Further, Zurich must prove Sandworm acted on behalf of Russia, which might appear obvious due to direct control of the Russian government on the group. Yet, cybersecurity company FireEye states that groups often carry out “activity potentially outside of state control.”[32] Thus, Zurich must produce evidence linking Sandworm’s actions to Russia. Perhaps most importantly, attribution methods used by private groups and governments cannot directly translate to insurance claims. Therefore, Zurich faces an evidentiary upward battle proving that Sandworm executed NotPetya on behalf of Russia, and even if they successfully demonstrate reasonable culpability, it might not be sufficient evidence for the court without individual names. For these reasons, it is unlikely that Zurich and the other insurance providers will avoid insurance payouts.
Conclusion
NotPetya does not satisfy the definition for an act of war, nor should the war exclusion apply to its consequences for several reasons. First, NotPetya fails to meet the criteria established both by Clausewitz and modern policymakers/politicians on what comprises war. Second, the technical design, target, and timing of NotPetya all suggest it aimed to target Ukraine. Thus, it is likely that the impact on US companies was an unforeseen byproduct. This means that NotPetya did not originate as act of war against the United States and should not be treated as such. Finally, even if NotPetya fit the criteria of an act of war, insurance providers would face a difficult battle proving this during their day in court due to burden of proof and issues with attribution. In conclusion, NotPetya was not an act of war and insurance companies will probably have to pay to cover the event. However, while the war exclusion clause will not likely apply to these cases, this will not prevent insurance companies from improving their policies in the future. Therefore, it is vital that the courts and/or US government establish standard procedure of what constitutes an act of war for cyberattacks, so insurance providers and their beneficiaries know what their policies do and do not cover to prevent future miscommunication.
[1] Eternalblue and Mimikatz were tools the attackers utilized to execute NotPetya. Both are related to Microsoft Windows vulnerabilities.
[2] Mike McQuade, “The Untold Story of NotPetya, the Most Devastating Cyberattack in History,” The Wired,August 22, 2018, https://www.wired.com/story/notpetya-cyberattack-ukraine-russia-code-crashed-the-world/.
[3] Michael Menapace, “Property Insurance, Cyber Insurance, Coverage and War: Losses From Malware May Not Be Covered Due to Your Policy’s Hostile Acts Exclusion,” The National Law Review IX, no. 69 (March 2019), https://www.natlawreview.com/article/property-insurance-cyber-insurance-coverage-and-war-losses-malware-may-not-be-0.
[4] Menapace, “Property Insurance.”
[5] Thomas Rid, “Cyber War Will Not Take Place,” Journal of Strategic Studies 35, no. 1 (October 2011): 5–32, https://www.tandfonline.com/doi/full/10.1080/01402390.2011.608939?scroll=top&needAccess=true.
[6] Rid, “Cyber War.”
[7] Daniel W. Woods and Jessica Weinkle, “Insurance Definitions of Cyber War,” The Geneva Papers on Risk and Insurance- Issues and Practice 45, (May 2020): 639–656, https://link.springer.com/content/pdf/10.1057/s41288-020-00168-5.pdf.
[8] Woods and Weinkle. “Insurance Definitions.”
[9] Rid, “Cyber War.”
[10] Steven Aftergood, “What is an Act of War In Cyberspace,” Federation of American Scientists, October 16, 2017, https://fas.org/blogs/secrecy/2017/10/war-cyberspace/.
[11] NotPetya did not destroy infrastructure, it did disrupt infrastructure. Yet, disruption of infrastructure does not fit into Lettre’s definition and will not be considered.
[12] Calculation done by hand.
[13] Sarah Crawford, “Costs of NotPetya,” Information Security Presentation, Spring 2021 and hand calculations.
[14]After 9/11, violent terrorist attacks began to be considered an act of war, as terrorist attacks are not state sponsored and thus fell outside traditional definitions of what war is. This is why 9/11 did not apply to war-exclusion and insurance payouts were given. However, insurance policies adjusted following 9/11 alongside definitions of war. Hence, acts of terror are now potentially considered exempt from insurance claims because war-exclusion can sometimes apply.
[15] James Lewis, “Assessing the Risks of Cyber Terrorism, Cyber War and Other Cyber Threats,” Center for Strategic Studies, December 2002, https://csis-website-prod.s3.amazonaws.com/s3fs-public/legacy_files/files/media/csis/pubs/021101_risks_of_cyberterror.pdf.
[16] Matthew McCabe, “NotPetya Was Not Cyber ‘War’,” MarshMcLennan. August 2018, https://www.mmc.com/insights/publications/2018/aug/notpetya-was-not-cyber-war.html.
[17] Sean Sullivan, “Obama: North Korea hack, ‘cyber vandalism,’ not ‘act of war’,” Washington Post, December 21, 2014, https://www.washingtonpost.com/news/post-politics/wp/2014/12/21/obama-north-korea-hack-cyber-vandalism-not-act-of-war/?noredirect=on.
[18] Mike Milliken, “Insurance to Fully Cover Sony’s Cyber Attack, Says CEO,” Insurance Journal, January 12, 2015, https://www.insurancejournal.com/news/national/2015/01/12/353835.htm.
[19] Karan Sood and Shaun Hurley, “NotPetya Technical Analysis- A Triple Threat: File Encryption, MFT Encryption, Credential Theft,” Crowdstrike, June 29, 2017, https://www.crowdstrike.com/blog/petrwrap-ransomware-technical-analysis-triple-threat-file-encryption-mft-encryption-credential-theft/.
[20] Andy Greenburg, “The Petya Plague Exposes the Threat of Evil Software Updates,” The Wired, July 7 2017, https://www.wired.com/story/petya-plague-automatic-software-updates/.
[21] Larry Loeb, “NotPetya Operators Installed Three Backdoors on ME. Doc Software Server Before Activating Malware,” Security Intelligence, July 10, 2017, https://securityintelligence.com/news/notpetya-operators-installed-three-backdoors-on-m-e-doc-software-server-before-activating-malware/.
[22] Matthias Williams and Pavel Polityuk, “Ukraine Says NotPetya hackers likely behind Badrabbit attack,” Reuters, October 31, 2017, https://www.reuters.com/article/us-cyber-summit-ukraine-idUSKBN1D02D1.
[23] Woods and Weinkle. “Insurance Definitions.”
[24] Woods and Weinkle. “Insurance Definitions.”
[25] “NotPetya: A Warlike Exclusion?” The Council of Insurance Agents & Brokers, May 2, 2019, https://www.ciab.com/resources/notpetya-a-war-like-exclusion/.
[26] Jon Bateman, “War, Terrorism, and Catastrophe in Cyber Insurance: Understanding and Reforming Exclusions,” Carnegie Endowment for International Peace, October 1, 2020, 11, https://www.jstor.org/stable/resrep26177.5?seq=2#metadata_info_tab_contents.
[27] Adam Shniderman, “Prove it! Judging the Hostile-or-Warlike-Action Exclusion in Cyber-Insurance Policies,” Yale Law Journal Forum, October 15, 2019, https://www.yalelawjournal.org/pdf/Shniderman_ProveIt_46vzsvqt.pdf.
[28] Bateman, “War, Terrorism, and Catastrophe.”
[29] Bateman, “War, Terrorism, and Catastrophe.”
[30] Andy Greenberg, “The White House Blames Russia for NotPetya, the “Most Costly Cyberattack in History,” The Wired, February 18, 2018, https://www.wired.com/story/white-house-russia-notpetya-attribution/#:~:text=The%20attribution%20of%20NotPetya%20to%20Russia%20represents%20a,attribution%20call%20for%20them%20to%20make%2C%22%20says%20Rid.
[31] Greenberg, “The White House.”
[32] Greenberg, “The White House.”




